
Hello, I am Lee Yoon-sang from the DevOps team at WhaTap Labs. There is an active movement to shift legacy infrastructure to the cloud in various industries around the world. In 2019, the policy was revised to allow public institutions to adopt the cloud, and the 'Cloud Security Certification' system was established to objectively evaluate cloud services to address the concerns of security-sensitive public institutions.
In order to provide cloud services to public institutions, it is necessary to obtain 'security certification'. In order to provide services to public organizations, WhaTap Labs has acquired the CSAP (Cloud Security Certification) certification in about half a year, and we would like to share the certification process through this blog.
What is Cloud Security Assurance Program?
It is a system that has been implemented since July 2016 to provide private cloud services with proven stability and reliability to public institutions, and to resolve users' security concerns and secure the competitiveness of cloud services by conducting objective and fair cloud service security certification.
* The following description is based on the SaaS simple grade certified by WhaTap, so please refer to the Korea Internet & Security Agency's Cloud Security Certification System website for other details.
Types of Evaluation and Certification
Certification Types
- IaaS and DaaS: Valid for 5 years
- SaaS Standard: Valid for 5 years
- SaaS Simple : Valid for 3 years
Assessment Types
- Initial assessments are conducted when you first obtain your security certification, and may be conducted on an ongoing basis if you make significant changes during the certification period.
- Once certified through the initial assessment, the certification is valid for 5 years (3 years for SaaS Simple Tier).
- Post-assessment is an assessment to check whether the cloud service security assessment and certification standards are continuously complied with after obtaining security certification, and is conducted annually within the certification validity period (3~5 years).
- Renewal evaluation is conducted when you want to extend the certification for cloud services before the expiration of the security certification validity period (3~5 years)
- * If you pass the renewal evaluation, the validity period of 3~5 years is granted again.
Certification Criteria
SaaS Simple Level Certification consists of 30 control items in 11 fields as additional protection measures for administrative, technical, and public institutions.
(Detailed items can be found in the attachment on the Korea Internet & Security Agency website)
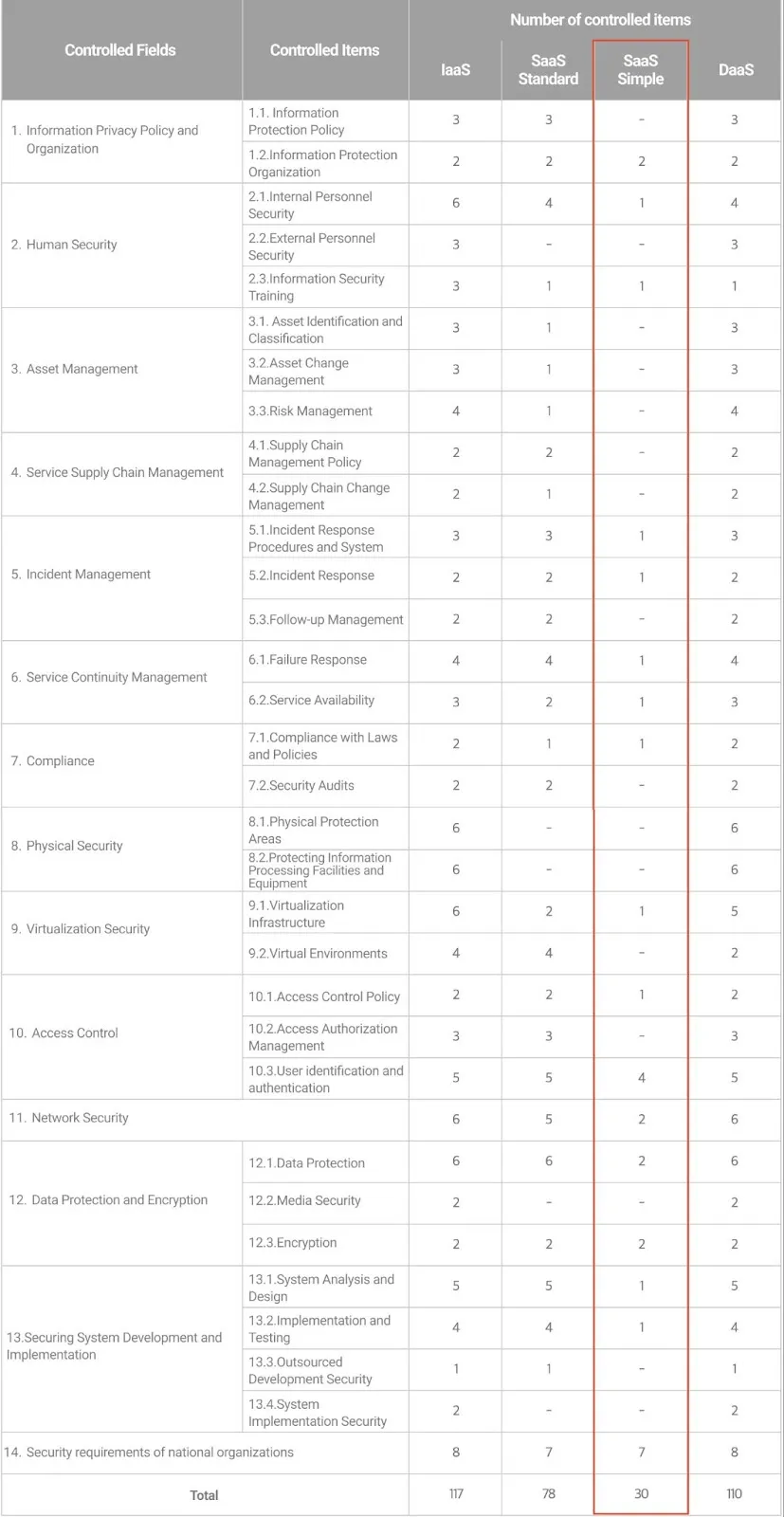
Source: Korea Internet & Security Agency Cloud Security Certification Program website
Assessment and Certification Process
The image below is based on the initial assessment. For the post-assessment, we start with the Assessment, Authentication step.
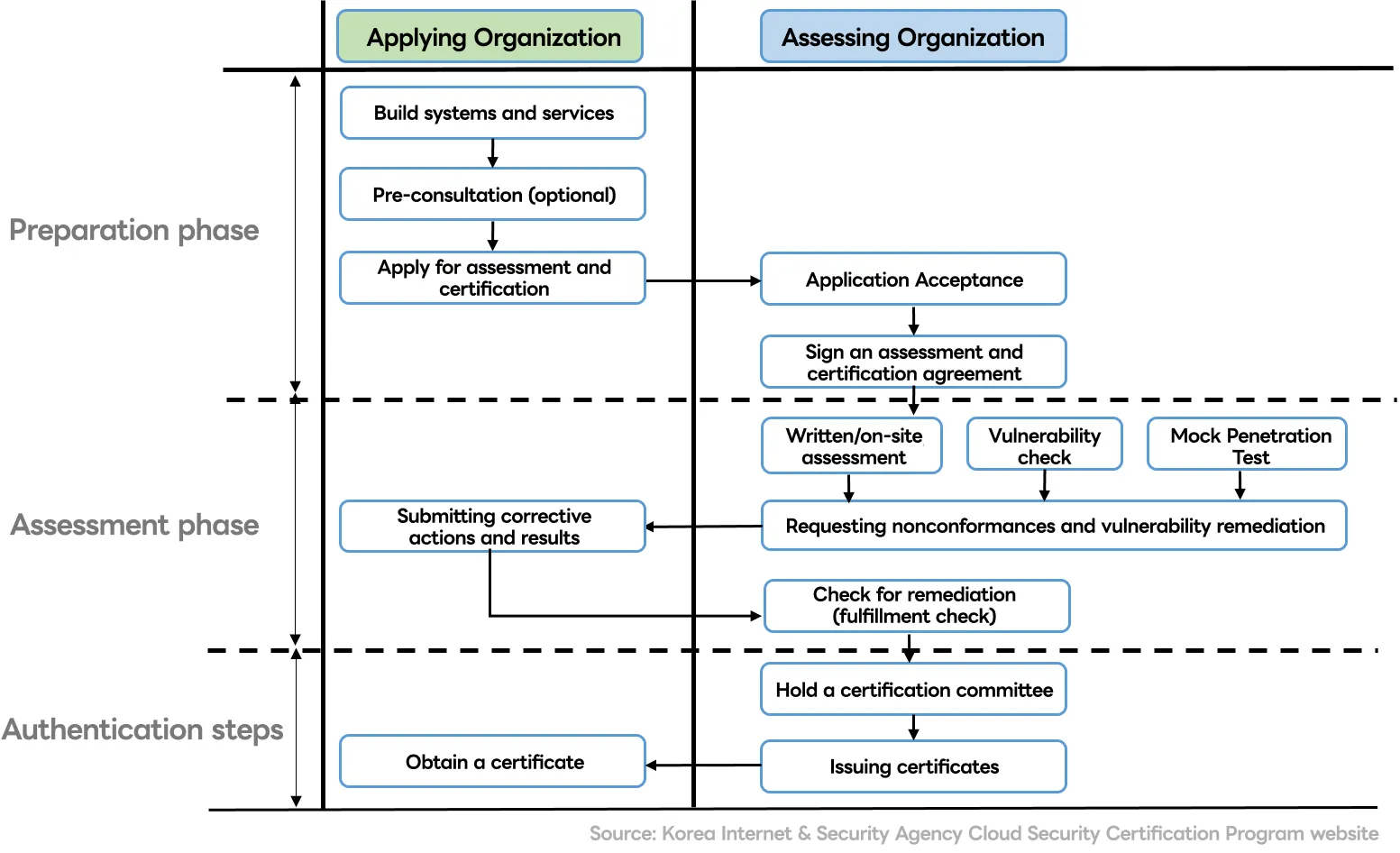
Source: Korea Internet & Security Agency Cloud Security Certification Program website
- For SaaS Simple Tier (14 days in total), it is conducted in the following order: "Pre-consultation 2 days → Written/on-site evaluation (4 days) - Vulnerability check (4 days) (simultaneous) 4 days → Mock penetration test 5 days → Implementation check 3 days".
* If vulnerabilities are found after the pre-consultation, you apply for certification by taking action, and the implementation check is carried out by remediating the vulnerabilities found in the certification evaluation stage, so the above schedule only includes the time when the check is actually carried out, so the time to complete the actual certification may take at least two months and up to half a year or more.
So far, we have briefly explained the "Cloud Security Certification Program", and next, we will explain the certification process at WhaTap.
Procedure
1.Apply for pre-consultation
In order to proceed with the certification smoothly, WhaTap received pre-consultation. To apply for pre-consultation, we downloaded the documents required for pre-consultation from the Korea Internet & Security Agency's Cloud Security Certification System archive, filled them out, and applied via email.
(Since the inspection team is not available for inspection immediately after application, you should refer to the target date for completing the certification. In the case of WhaTap, the pre-consultation took place 3 weeks after application.)
The pre-consultation was conducted by three people: one person in charge of certification, one person who conducted the written/on-site assessment, and one person who checked the vulnerabilities, and lasted for two days. After the pre-consultation, we received a report with vulnerabilities, and we prepared for this inspection by correcting the vulnerabilities.
2. Proceed with the inspection
We applied for the main inspection by fixing all the vulnerabilities identified during the pre-consultation.
The inspection was conducted by a total of seven people, including one certification manager, one written/on-site assessment, four vulnerability assessments (two CCEs and two CVEs), and one source code assessment, and lasted for four days. The inspection also included a penetration test, which was conducted online by a penetration assessment team (two people) for four days starting the day after the inspection was completed.
Unlike the pre-consultation, the main inspection was more thorough and detailed, with 4 days of Q&A and demonstrations, resulting in 8 written/on-site assessment non-conformances and 10,542 vulnerabilities (including source code) with remediation requirements.
The remediation must be 100% completed within 30 days, and if it is difficult to complete the remediation within the timeframe, it can be extended by sending a remediation extension letter (up to 3 months).
WhaTap completed all the measures within 30 days and applied for the fulfillment check.
3. Implementation Inspection
The fulfillment check is a check to confirm whether the vulnerabilities found in the main inspection have been fixed, and it does not include assets newly created during the implementation.
The Transition Inspection was attended by almost the same number of people as the main inspection: one certification lead, one written/on-site assessment, two vulnerability assessors (CCE and CVE), and one source code assessor, and lasted for three days. The penetration was conducted online by the penetration assessment team (2 people) on the same day as the fulfillment check date.
As the principle of certificate issuance is 100% action, WhaTap developers and each person in charge made every effort to take action on all vulnerabilities found during the three days of the fulfillment check.
4. Completion
After 3 inspections: pre-consultation, main inspection, and fulfillment inspection, we finally got the certificate!

WhaTap received a cloud security certificate!
Wrapping Up
All of us at WhaTap have been preparing for a long time and have been able to get the certification in one go.
Since it is a certification that we have put a lot of effort into, why don't you introduce "Monitoring Service WhaTap" with enhanced security with peace of mind to public organizations?
.svg)
.svg)






