Last year, the government announced zero trust guidelines and is encouraging the introduction of zero trust architectures. I'll tell you in detail what zero trust architecture is and how Watab can be used in this environment!
- Zero trust promotion background
The spread of mobile and cloud has created a remote telecommuting environment, and COVID-19 has accelerated the non-face-to-face society. Due to the increasing number of users, devices, and devices, permission management has become more complicated and difficult to manage.
Attacks that take advantage of gaps in implicit trust policies in perimeter security, such as insider collusion and privilege theft, have increased. The limitations of perimeter-based security models are being revealed, and a new security paradigm is needed. - Zero trust concept
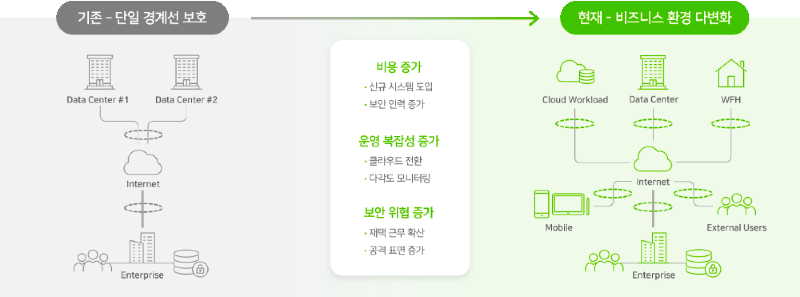
Traditional perimeter-based security models begin with the assumption that internal network access requirements (users, devices, etc.) can be trusted to a certain extent. Zero Trust, on the other hand, starts with the assumption that hackers can exist anywhere inside or outside the network, and all connection requests are unreliable.
All data and computing services that need to be protected are separated and protected into individual resources, and after connecting to a single resource, activities are only possible for the specified permission, and penetration is limited by continuous authentication when additional access to nearby resources is required.
- Zero-trust architecture
Zero-trost does not mean a specific product line or solution, but rather a security paradigm based on a common understanding across the entire organization. The philosophy of zero trust must be embedded in all solutions introduced or newly introduced into the enterprise network, and each individual solution must organically collaborate to continuously authenticate normal users of the corporate network to give trust and manage access to corporate resources in detail.
- The basic philosophy of zero trust
- Don't trust any kind of access (allow resource access after explicit trust verification)
- Consistent and centralized policy management and execution of access control decisions are required
- Management and strong authentication for users and devices
- Detailed access control through resource classification and management (minimum authorization)
- Create logical boundaries, allow session-by-session access, and apply communication protection technology
- Continuous verification and control of reliability through monitoring and logging of all conditions
- Key principles for implementing zero trust
- Strengthening the certification system (1, 2, 3, 6 in basic philosophy)
- Establish an authentication policy by setting the reliability of various resource access entities (determining the terminal used, asset status, environmental factors, access location, etc.) as a key factor
- Microsegmentation (2, 4, 5 in basic philosophy)
- Deploy development resources in a separate network area protected by a secure gateway, and perform continuous trust verification for various access requests
- Software-defined boundaries (1, 2, and 5 of basic philosophies)
- Dynamic network configuration based on policy engine decisions using software-defined boundary techniques, and data channel formation for resource access after securing user terminal trust
When introducing a zero trust architecture, three core principles must be set up and managed so that they work properly, focusing on 6 basic philosophies.
- Effects of introducing zero trust
I'll use a remote attack or insider threat scenario as an example.
If a malicious attacker hijacks a user device using Internet-based malicious code, or if the attacker is an insider with malicious intent, it is possible to continue to damage data stores, etc. through network access, privilege escalation, and lateral movement using normal user credentials illegally in an existing corporate network environment. It's there.
However, in a zero-trust environment, lateral movement is not possible because forged user credentials and devices are assumed to be suspicious until proven to be normal. Even if attackers pass user credentials and device authentication, access to data is restricted according to security policies, roles, etc., and access control is carried out in detail, making it difficult to work with sensitive data.
Furthermore, by analyzing user behavior through continuous logs and monitoring, additional authentication requirements and dynamic access restrictions are possible in the case of suspicious users. Even if some damage occurs, the range of affected resources will be reduced, and rapid response is possible.
- Usability of WhaTap in a zero-trust architecture
Zero-trust architectures require monitoring of all states. All states include various states of access subjects (users and devices), resources (data, applications, servers, networks, cloud services, etc.), and policy servers. Instead of simply monitoring logs, events, etc., it is necessary to integrate multiple modules, servers, and services in an MSA environment to comprehensively monitor.
This status information must be monitored so that the current state can be understood numerically and visually, and future detailed analysis and audit must be possible through logs. Monitoring data and logs are a base data that can continuously verify the reliability of all access subjects and corporate networks currently connected, and dynamically manage access. This data requires long-term storage for later analysis, and its integrity must be guaranteed.
The current state of servers and applications can be grasped through various monitoring data from WTAP, and continuous auditing is possible through log monitoring. Immediate response is also possible through various notifications.
- Zero-trust architecture applied to WhaTap
WTAP implements several functions reflecting the basic philosophy of zero trust.
- Identifier and ID multi-factor authentication support
- Since it supports MFA authentication, intrusion is impossible simply by stealing ID and PW.
- User access control at a sophisticated level
- Minimum permissions can be granted through project-specific role-based access control (RBAC).
- For more information on access control blog postPlease refer to!
- User behavior tracking
- User behavior can be monitored.
- User behavior monitoring enables additional authentication requirements or dynamic access restrictions in the event of abnormal activity.
- data security
- Passwords are encrypted using one-way SHA-256, and other personal information (name, phone number, company name) is encrypted using AES-256.
- We are encrypting the disk to protect the monitoring data even if other means of defense fail.
As the limitations of traditional perimeter-based security models become clear, the importance of zero trust is being emphasized. In a zero-trust architecture configuration suitable for an enterprise, WhaTap can greatly help with related monitoring and visibility.
.svg)