

What is the first thing an attacker does after breaking into a server through any number of methods?
The first thing they do is delete logs to cover their intrusion tracks. They remove any trace of when, how, and through what route they got in, disrupting tracking. This is because if their intrusion method is publicized, they cannot use the same method to break in.
Therefore, you need a secondary backup of your logs in real time to counter attackers' attempts to delete them. The logs you should focus on are access records. Access records contain the [who, when, where, and how].
Keeping and inspecting them is required by law. You can find it in Article 8 (Retention and Inspection of Access Records) of the "Standards for Measures to Secure the Safety of Personal Information", which was revised this year.
- 1. The personal information processor shall keep and manage records of access to the personal information processing system of the personal information handler for at least one year. However, in the case of any of the following subparagraphs, it shall be kept and managed for at least two years.
- In the case of a personal information processing system that processes personal information about 50,000 or more information subjects
- In the case of a personal information processing system that processes uniquely identifiable or sensitive information
- If you are a telecommunications service provider that has registered under Article 6 (1) of the Telecommunications Business Act as a personal information processor or reported under the provisions of the same Article
- 2. The personal information processor shall check the access records of the personal information processing system at least once a month in order to respond to the misuse, loss, theft, leakage, forgery, alteration, or damage of personal information. In particular, if the downloading of personal information is confirmed, the reason must be confirmed in accordance with the internal management plan, etc.
- 3. The personal information processor shall take measures to safely store the access records so that the access records are not forged, altered, stolen, or lost.
In conclusion, access records of personal information processing systems should be kept for at least one or two years and checked at least once a month to ensure their integrity during the retention period.
Types of access records left in the Linux syslog
Linux has a syslog service that generates and manages log messages. This allows you to view a variety of logs, including boot messages, remote access history, user access history, login history, and more.
The primary logs we focus on from a security perspective are user access records. You can see information about when, where, who, and how they accessed, and you can see a variety of monitoring scenarios.
You will know if unauthorized users are accessing your production servers from unauthorized locations. Based on these logs, you can take action, such as blocking related IPs through firewalls, security groups, etc.
Here's what the Linux syslog looks like for connection history logs.
1. Login logs
- Login log using pem key Feb 7 05:58:04 [host_name] sshd[0000]: **Accepted publickey** for [login_user] from [login_ip] port [login_port] ssh2: RSA SHA256:asdkjhfasdfkjh
- Login log using password Feb 7 05:49:49 [host_name] sshd[0000]: Accepted password for [login_user] from [login_ip] port [login_port] ssh2
- Password Failure Log Feb 7 06:12:10 [host_name] sshd[0000]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=[login_ip] user=[login_user]
2. Logout logs
- Feb 7 05:48:27 [host_name] sshd[0000]: Disconnected from user [login_user] [login_ip] port [login_port]
Through the above logs, you can check various scenarios, such as whether a user without PEM key authorization accessed the production server or accessed the root account. You can also monitor brute force attacks through the number of failed password attempts.
Monitoring security logs with WhaTap Log Monitoring
You can check logs through various commands such as tail, cat, more, etc. in the terminal, but the downside is that you need to connect to the server directly.
With WhaTap Log Monitoring, you get log monitoring that allows you to analyze heterogeneous logs, monitor via dashboards, set alerts, and more from one screen.
It allows you to collect, aggregate, and analyze large amounts of data from your enterprise in one place and streamlines related security workflows. Additionally, it provides operational capabilities such as compliance reporting, incident management, and dashboards that prioritize threat activity.
For example, it can be linked with the internal HR system to monitor various scenarios, such as checking whether employees on vacation have access to the production DB, or if employees in the office are VPNed to an external or overseas network.
At WhaTap Labs, we are using the Flex Board feature to monitor security logs. We are using the syslog collection feature of server monitoring, and we have included the history log in the syslog through the profile feature of Linux.
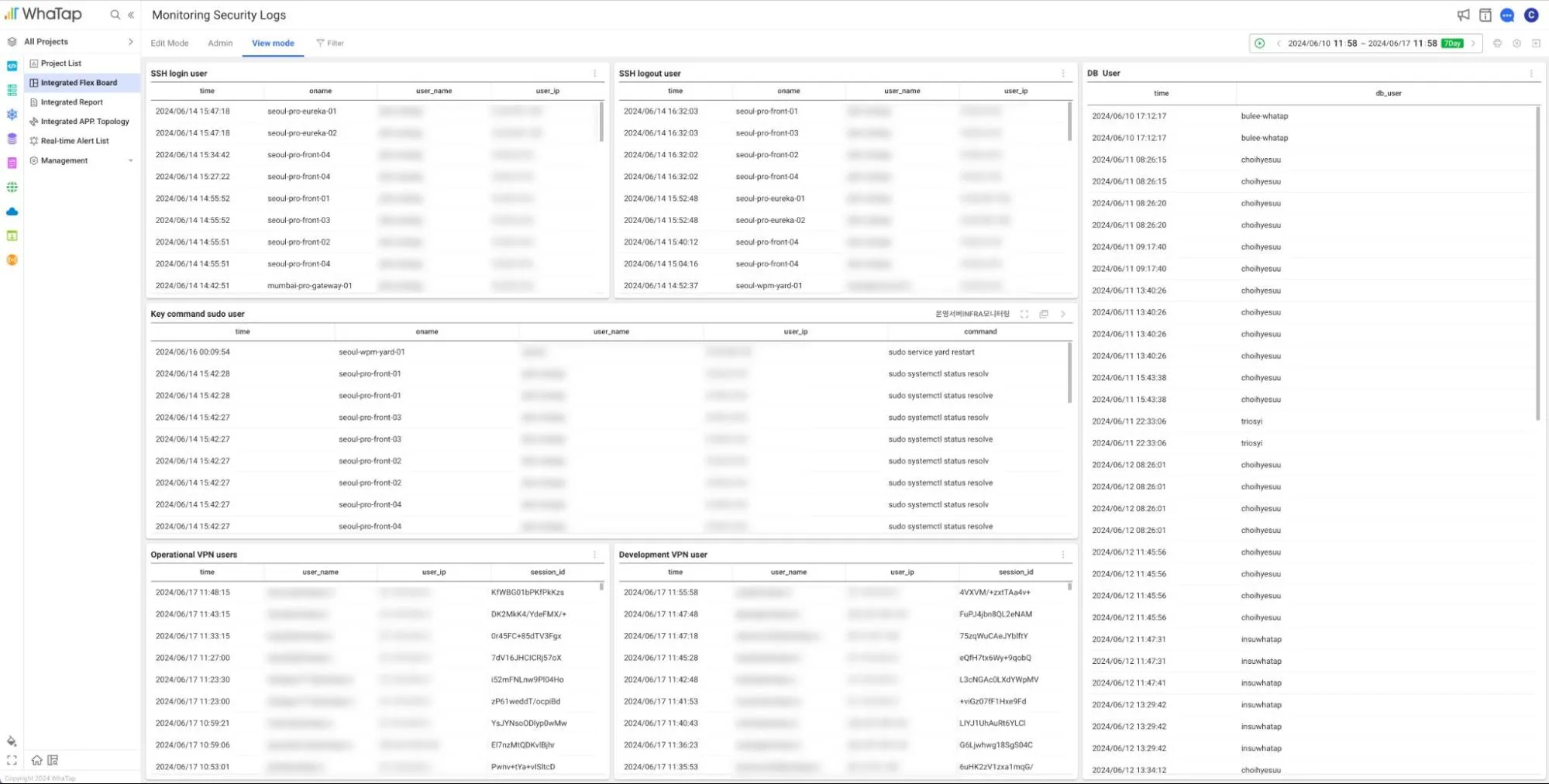
SSH login users can give you an idea of who has access to your production servers, which can inform your monthly authorization adequacy audits. By comparing SSH login times and logout times, you can determine how long they are on the server, and a series of short stays should raise suspicion.
We also check users running with root authorizations in real-time to see if they need those authorizations, for example.
In addition, we are integrating WhaTap notifications with a third-party, Telegram, to check for the use of internally specified cautionary commands such as system wipe, file owner change, and process kill.
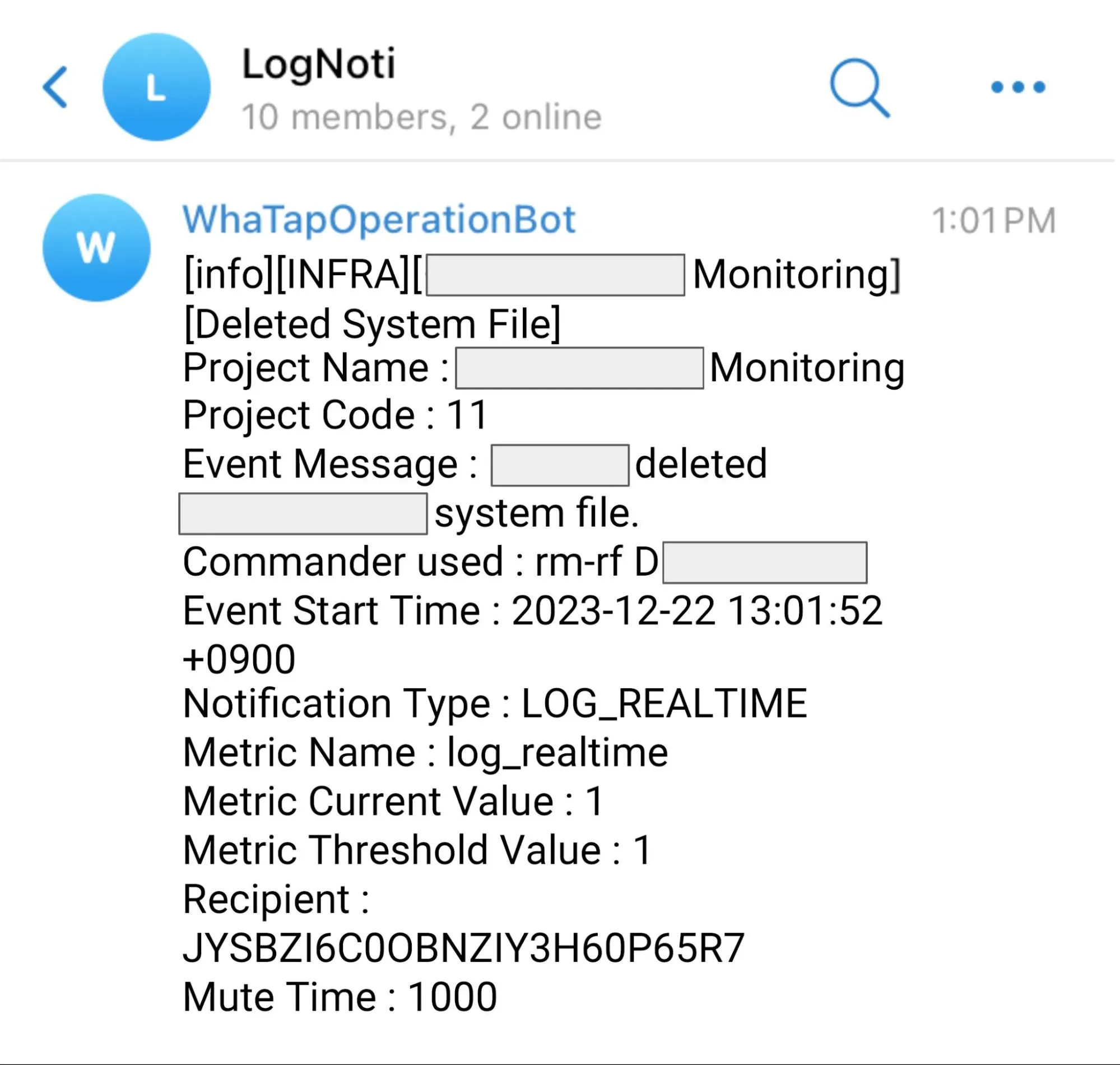
These alerts allow you to see which users have accessed which servers and performed certain actions, and you can see in real-time if they have done anything operationally or security-critical. In the event of an intruder, you will know immediately what they have done to affect your service.
WhaTap does not officially allow employees to work from home, which is why we only allow VPN access inside the office. If a VPN is accessed from outside the office, we are notified immediately through a notification.
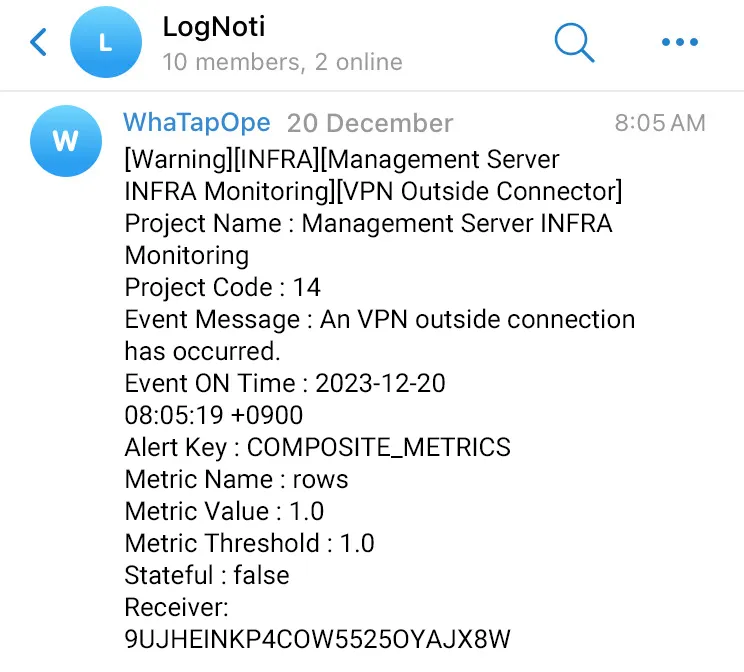
In addition, various scenarios can be identified through the logs collected and monitored through the dashboard. You can streamline your security workflow through heterogeneous analysis by collecting not only syslogs but also logs from internally installed security equipment, etc.
.svg)
.svg)






