
In the last article, we briefly covered the types of encryption. In this article, we will cover real-world use cases for different encryption techniques. Today's topic is "envelope encryption," a use case for the symmetric key algorithm.
We have talked about symmetric-key encryption before, explaining that if you do not protect your keys well, you are communicating in plain text. What is the safest way to store your most valuable possessions? Instead of keeping it in a safe and guarding it, we leave it in a bank. Envelope encryption is a way to entrust a secure cloud service provider (CSP) with the management of your encryption keys, just as you would entrust your money to a bank.
Introduction to envelope encryption
Envelope encryption can be summarized in one sentence: "Encrypt not only the message, but also the encryption key.” To illustrate, let's compare it to traditional symmetric-key encryption.
In traditional symmetric-key cryptography, you store the key wherever you think it is safest and use it to encrypt and decrypt.
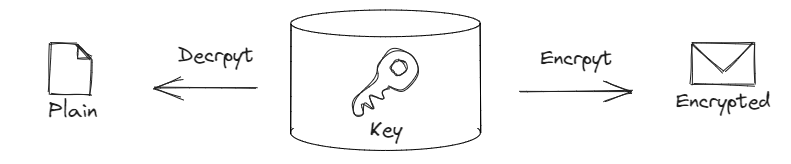
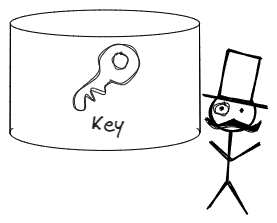
However, the problem with this approach was that if a malicious user stole the key, they could decrypt all of the messages.
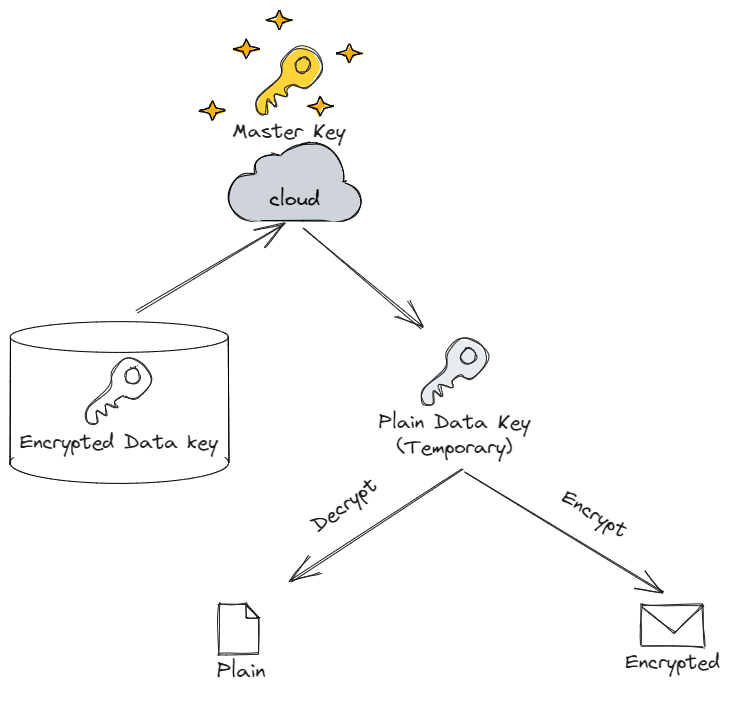
What if we encrypted the encryption key just like the message? Even if a malicious user were to steal the key, they would not be able to decrypt the message if the "encryption key of the encryption key" was kept securely. Since the naming is confusing, we will refer to the key that encrypts the message as the data key and the key that encrypts the data key as the master key.
The process of envelope encryption with a combination of data key and master key looks like the following.
- Encrypt and store the data key with the master key.
- Decrypt the data key when a decryption request comes in.
- Decrypt the plaintext with the decrypted data key.
- Delete the decrypted data key.
Since the encryption key is immediately deleted after the decryption is performed, the risk of capture is greatly reduced. We may have found the perfect algorithm, but if the master key is stolen, the plaintext is still exposed. You cannot just re-encrypt the master key, re-encrypt that key, and repeat the process ad infinitum. You are better off protecting your data keys with the effort of managing two separate keys.
But if a CSP like AWS holds the master key for you, that is a different story. Even the user of the data key does not know what the master key is - the API only tells them the result of the decryption of the data key. Here's a simple illustration.

It is much harder to steal keys than it was before envelope encryption, because the decrypted data key only exists for the short time it takes to perform the decryption of the message. As long as you protect the data key during that time, your CSP will take care of the rest.
Using cloud-managed keys
There is an even stronger key management policy than the previous methods. It is to not decrypt the key at all. How can you operate if you do not know the encryption key? In cloud environments, there are quite a few cases where decryption is not necessary.
For example, imagine encrypting data in a cloud DBMS like AWS RDS. The infrastructure that makes up the database is all managed by the cloud provider, so users do not have to manage the encryption keys. The cryptographic keys managed by the CSP are highly protected and rotated regularly. It is convenient to use CSP-managed keys for encryption of disks, DBMS, object storage, etc.
In today's post, we learned about the "envelope encryption" technique that secures encryption keys, a weakness of public key cryptography. WhaTap uses envelope encryption to protect some information, and it is something you should consider implementing when developing a cloud-native application like WhaTap.
.svg)
.svg)






